For many of us, email is the most vital communication tool we use in the course of our day-to-day business, but it is also one of the biggest security vulnerabilities we open ourselves up to!
The technology that drives email is ancient (in tech terms!) and was initially developed in the 1960s. While it has evolved somewhat since then, there are many security problems that are inherent to its design – the most significant being spam and malicious attachments. Almost all instances of virus infection we encounter are the result of these spammy and malicious emails.
To help you mitigate the risk of getting all your data encrypted because of a ransomware bug or ending up with viruses on all your company computers I’ve put together my beginner’s guide to identifying dodgy emails.
Phishing Emails

The most common type of fake email I see (and the most likely to trick someone) are phishing emails – a term that became popular in the 80’s when hackers thought it was cool to replace ‘F’s with ‘Ph’s. These emails are an accurate looking knock-off of something you’d normally expect to receive, designed to lure you into clicking a link in the message or opening an attachment.
The topics of these emails and the companies they impersonate are vast, but in my experience the most convincing ones that catch people out are the following:
- Auspost or other shipping companies like DHL – Claiming your package delivery has been postponed and that you need to click a link to resolve a problem.
- Airlines – Claiming your flights have been moved or cancelled, again needing you to click a link to action something.
- ATO or ASIC – Claiming there is a problem with your BAS or business registration and once again requiring you to click a link to resolve.
- Unknown Business – Claiming that there are unpaid invoices you owe them or that they are having problems paying you, usually these have an attached .zip file with the virus inside.
If you see any of these it should raise a big red flag and you should try and confirm your suspicions. Luckily, I’ve put together some easy to follow instructions to figure out whether an email is authentic that pretty much anyone should be able to follow.
Don’t click the link.
Let’s look at an example of an email one of our clients received this week:
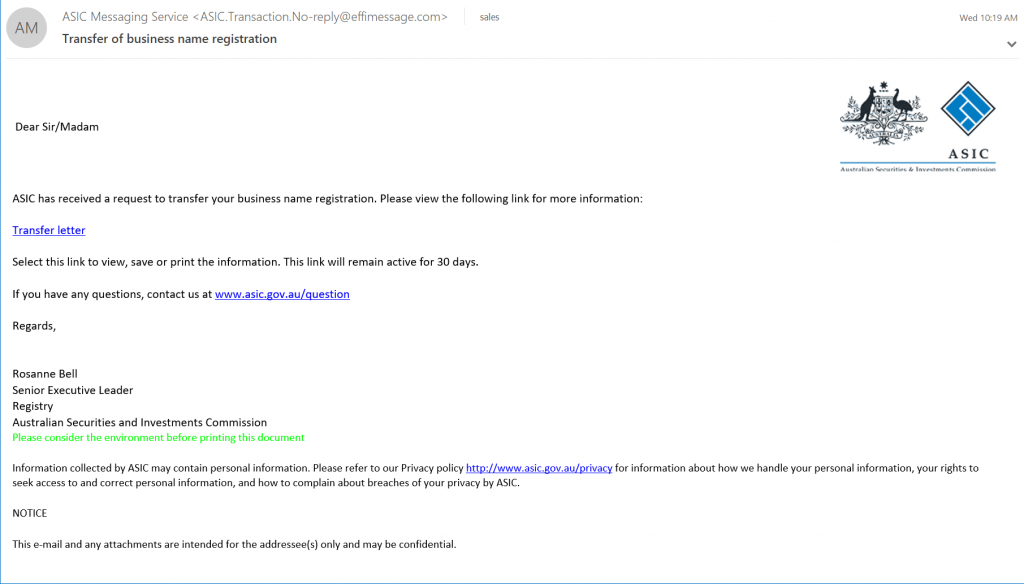
At a glance this looks innocent enough right?Bbut there are a number of issues that are very obvious – once you know where to look. The very first thing to check is the ‘From:’ line, which in this case reads:
(ASIC Messaging Service <ASIC.Transaction.No-reply@effimessage.com>)
Take a look at that email address! Notice how it is from ‘@effimessage.com’ and not a ‘.gov.au’ address? This would be enough for me to delete it and move on – but there is another easy thing to check if you are still not 100% sure if it’s legitimate. The link to the ‘Transfer letter’ in the middle of the page is clearly what they are trying to get you to click on, but if you just hover over the link (without clicking it!) it will show you where it is trying to take you. Check the screenshot below:
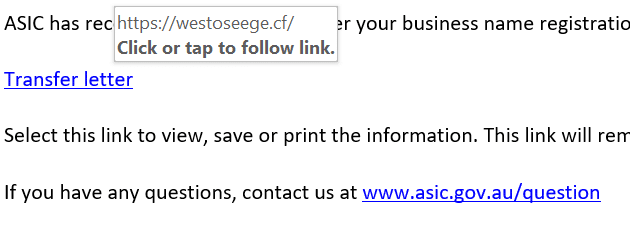
The first thing to check is the ending (known as a “tld” or “top level domain”) of the site it’s trying to send you to. In this case it is a ‘.cf’ and not a ‘.gov.au’ or even .com.au. Then look at the domain name itself – ‘westoseege’ – what even is that? This email is now confirmed 100% dodgy at this point and we should definitely delete it and move on.
Check for dodgy attachments
The next thing you need to learn about to protect you and your company is how to identify malicious attachments.
Take a look at this example:
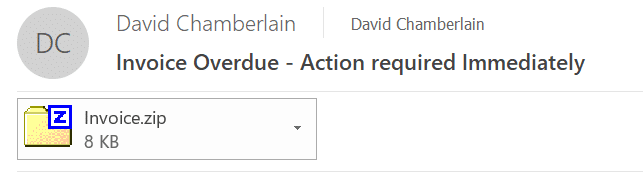
When dealing with zip file attachments the correct response nearly 100% of the time is to delete the message and ignore it, but if you do want to verify the authenticity of a zip attachment (e.g. you are expecting an email with a bunch of documents) there is an easy way to do it. You should be warned though – but you need to be careful to not infect yourself in the process! Make sure you follow these instructions carefully.
Opening a zip file to view its contents isn’t enough to infect your computer – but opening any of the files inside it is dangerous.
So let’s open this attachment to verify that it is actually a virus.
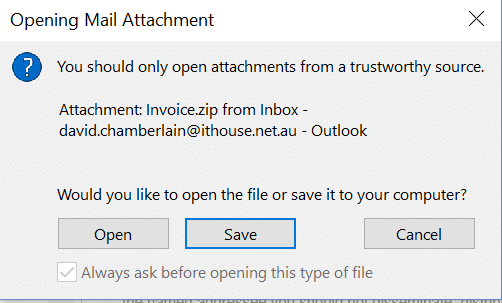
Note here that the latest versions of Outlook will actually warn you before opening zip files. Here I have chosen “Save” and then navigated to the folder in which the attachment is stored. Double click to ‘open’ the zip file in Windows Explorer and you should see something like this.
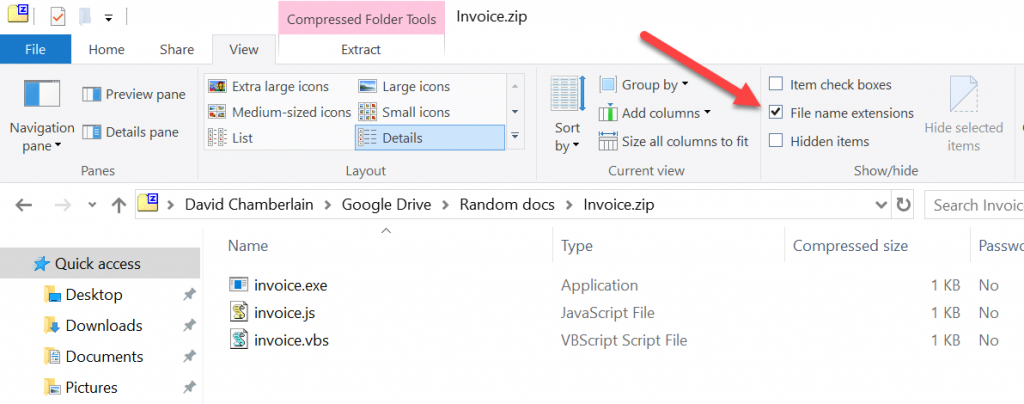
Once you open the zip file, click the View tab at the top and choose the ‘Details’ view, then tick the ‘File name extensions’ check box. What we are looking for is the two or three character extensions after the file name, which in the example above are .exe, .js & .vbs. Don’t open any files with these extensions as they are commonly used to spread malware and in almost all cases you should generally only open .pdf, .docx or .xlsx files. from people that you trust.
Top 4 tips…
Here’s a summary of the key points for you to take away:
- Check the ‘From:’ field and make sure the address looks like it tied to the company (including the domain extension, e.g. .gov.au).
- Hover your mouse cursor over any links the email is wanting you to click and check if the link looks legitimate.
- Check the attachment – if it is a zip file consider just deleting it. You can double check with the steps above if needed.
- Most importantly if you are at all unsure about an email, get someone who is tech savvy (maybe us!) to verify it for you.
The IT House team offers customised staff training courses for teams that might be struggling to identify spam and malicious attachments. We can teach your staff how to identify dodgy emails as well as other Get in touch with us if this is something you’d like help with.
